Navigating the Terrain of Digital Map Attacks: A Comprehensive Exploration
Related Articles: Navigating the Terrain of Digital Map Attacks: A Comprehensive Exploration
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating the Terrain of Digital Map Attacks: A Comprehensive Exploration. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Terrain of Digital Map Attacks: A Comprehensive Exploration
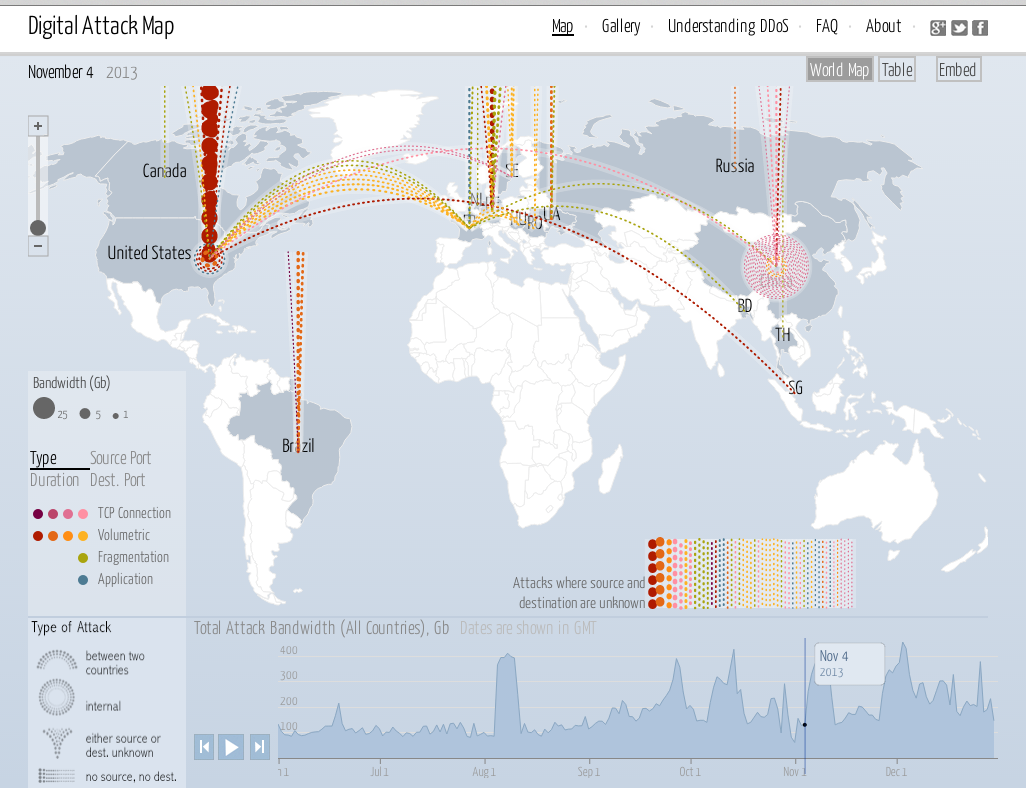
The digital world, with its interconnected networks and vast repositories of data, has become a fertile ground for various forms of cyberattacks. One such attack, often overlooked but potentially devastating, is the manipulation of digital maps. These attacks, targeting the underlying data and infrastructure of mapping services, can have far-reaching consequences, impacting navigation, emergency response, critical infrastructure, and even national security. This article delves into the intricacies of these attacks, exploring their methods, motivations, and potential impacts, while highlighting the crucial role of robust security measures in mitigating these threats.
Understanding the Vulnerability of Digital Maps
Digital maps, ubiquitous in our daily lives, rely on a complex web of data and systems. They draw upon a vast network of sensors, satellites, and user contributions to generate accurate representations of the physical world. This intricate infrastructure, however, presents a tempting target for malicious actors seeking to disrupt or exploit information.
Methods of Digital Map Attack
Digital map attacks can manifest in various forms, each targeting a specific vulnerability in the mapping ecosystem. These methods include:
- Data Manipulation: Attackers can alter the underlying data used to generate maps, leading to inaccuracies in location information, road closures, or the misrepresentation of points of interest. This can cause confusion and misdirection, potentially impacting navigation, emergency response, and even economic activity.
- Infrastructure Disruption: Attackers can target the servers or networks responsible for hosting and distributing map data, causing service outages or slowing down map loading times. This can significantly hamper navigation and access to real-time information, particularly in critical situations.
- Spoofing and Deception: Attackers can create fake locations, routes, or points of interest on maps, leading users astray or exposing them to danger. This can be particularly dangerous for individuals relying on maps for navigation in unfamiliar territories or during emergencies.
- Denial of Service (DoS) Attacks: Attackers can overload mapping servers with excessive requests, making them unresponsive and effectively denying legitimate users access to the service. This can have widespread consequences, particularly during peak traffic periods or during emergencies.
- GPS Spoofing: Attackers can interfere with GPS signals, causing devices to display incorrect location information. This can be used to misdirect individuals, vehicles, or even critical infrastructure like power grids.
Motivations Behind Digital Map Attacks
The motivations behind digital map attacks can vary significantly. Some attacks may be driven by:
- Financial Gain: Attackers can exploit vulnerabilities in mapping systems for financial gain, potentially targeting advertising revenue or manipulating financial markets based on misrepresented location data.
- Political Agitation: Attacks can be used to spread misinformation, sow discord, or undermine public trust in official sources of information. This can be particularly effective during times of political unrest or crisis.
- Espionage and Intelligence Gathering: Attackers can target mapping systems to gather sensitive information about infrastructure, military movements, or civilian populations. This information can then be used for espionage or to plan future attacks.
- Cyberterrorism: Attacks can be launched to disrupt critical infrastructure, cause widespread panic, or destabilize entire nations. This can be particularly devastating during times of conflict or natural disasters.
- Personal Revenge or Malice: Individuals with personal grudges or malicious intent can target mapping systems to cause harm or inconvenience to specific individuals or groups.
Impact of Digital Map Attacks
The consequences of digital map attacks can be far-reaching and potentially devastating, impacting various sectors and aspects of daily life:
- Navigation and Transportation: Misinformation or disruption of mapping services can lead to accidents, traffic jams, and delays in transportation. This can have significant economic and social consequences, particularly in urban areas with heavy reliance on navigation systems.
- Emergency Response: Inaccurate or unavailable map data can hinder emergency response efforts, delaying the arrival of help and potentially putting lives at risk. This can be particularly critical during natural disasters, terrorist attacks, or other emergencies.
- Critical Infrastructure: Attacks targeting mapping data related to critical infrastructure, such as power grids, water systems, or communication networks, can cause widespread disruptions and even lead to catastrophic failures.
- National Security: Digital map attacks can compromise sensitive information about military deployments, critical infrastructure, or civilian populations, potentially impacting national security and defense operations.
- Economic Impact: Attacks on mapping systems can disrupt supply chains, hinder economic activity, and cause financial losses for businesses and individuals.
Mitigating the Risk of Digital Map Attacks
To counter the growing threat of digital map attacks, a multi-pronged approach is required, encompassing:
- Data Security and Integrity: Implementing robust data security measures, including encryption, access control, and regular data audits, can help protect mapping data from unauthorized access and manipulation.
- Infrastructure Security: Securing the servers and networks responsible for hosting and distributing map data is crucial. This includes implementing firewalls, intrusion detection systems, and regular security updates.
- User Awareness and Education: Educating users about the potential risks of digital map attacks and encouraging them to be critical of the information they encounter can help prevent them from falling victim to misinformation or deception.
- Collaboration and Information Sharing: Sharing information about attacks and vulnerabilities between mapping providers, security researchers, and government agencies is essential for developing effective countermeasures and building a more resilient ecosystem.
- Developing and Implementing New Technologies: Investing in research and development of new technologies, such as blockchain and cryptography, can help create more secure and resilient mapping systems.
FAQs on Digital Map Attacks
Q: How can I tell if a map is being manipulated?
A: It is difficult to detect manipulated map data without specialized tools. However, some signs to be aware of include:
- Unexpected road closures or detours: If a map suddenly shows a road closed or diverted without any apparent reason, it could be a sign of manipulation.
- Inaccurate locations of points of interest: If a map shows a hospital, restaurant, or other point of interest in an incorrect location, it could be a sign of manipulation.
- Unfamiliar routes or paths: If a map suggests a route that seems illogical or unsafe, it could be a sign of manipulation.
Q: Can I rely on my phone’s GPS for navigation?
A: While GPS technology is generally reliable, it is vulnerable to spoofing attacks. If you are in an area with a high risk of GPS spoofing, it is advisable to use multiple navigation sources and be aware of your surroundings.
Q: What can I do to protect myself from digital map attacks?
A: You can take several steps to protect yourself:
- Use multiple navigation sources: Don’t rely solely on one mapping app. Use multiple sources to verify information and avoid relying on a single point of failure.
- Be critical of the information you encounter: Don’t blindly trust everything you see on a map. Use common sense and verify information from multiple sources.
- Keep your software up to date: Regularly update your mapping apps and operating system to patch security vulnerabilities.
- Be aware of your surroundings: Pay attention to your environment and be alert for signs of danger.
Tips for Mitigating the Risk of Digital Map Attacks
- Implement robust security measures: Invest in comprehensive security solutions that protect data, infrastructure, and user accounts.
- Conduct regular security audits: Periodically assess your systems for vulnerabilities and implement necessary security updates.
- Promote user awareness: Educate users about the risks of digital map attacks and encourage them to be vigilant.
- Collaborate with other organizations: Share information and best practices with other mapping providers, security researchers, and government agencies.
- Stay informed about emerging threats: Monitor security news and research to stay abreast of new attack methods and vulnerabilities.
Conclusion
Digital map attacks pose a growing threat to our interconnected world. By understanding the methods, motivations, and potential impacts of these attacks, we can take proactive steps to mitigate the risks. Implementing robust security measures, promoting user awareness, and fostering collaboration are crucial steps in building a more secure and resilient mapping ecosystem. As technology continues to evolve, so too will the tactics employed by malicious actors. Vigilance, adaptability, and a commitment to cybersecurity are essential in safeguarding our digital maps and ensuring the integrity of the information they provide.





Closure
Thus, we hope this article has provided valuable insights into Navigating the Terrain of Digital Map Attacks: A Comprehensive Exploration. We thank you for taking the time to read this article. See you in our next article!